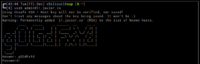
This pam module is product of Jordan Sissel [0] and it's so cool than I package it for Debian|Ubuntu, so.., on this tutorial I'll show you how to add captcha protection to your vps instances =)
Installation
$ sudo add-apt-repository ppa:chilicuil/sucklesstools
$ sudo apt-get update && sudo apt-get install libpam-captcha
Configuration
To enable this module, you'll need to edit /etc/pam.d/sshd and add to the first line the following:
auth requisite pam_captcha.so math randomstring
And then ensure than your /etc/ssh/sshd_config have the following options enabled:
PasswordAuthentication no
ChallengeResponseAuthentication yes
UsePAM yes
You can still use Password auth but it doesn't make a lot of sense, since automated scripts can request this method and avoid captcha, so it's better to disable it, in the other hand if you use ssh key based auth the captcha will be skipped
After ensuring your settings are correct, you'll need to reboot the ssh service:
$ sudo service ssh restart
And that's all, most automated attacks will be reject it.
Feel free to grab the modified source at:
https://github.com/chilicuil/pam_captcha
Or the original at [0], if you liked the post rate it =)
[0] http://www.semicomplete.com/projects/pam_captcha
Last edited by a moderator:
