Kokaku Kidotai
New Member
Good day gentlemen,
What could be the reason for the "auditd" process to use almost 400% (roughly 397%) for over 425 hours (431 hours before being suspended)? The process "auditd" was called by the system user "Apache". The box is running CentOS 6 with zPanel, two sites and a private PPTP VPN.
top:
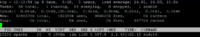
Any idea where to start the investigation from? I totally have no idea but I want to solve this issue.
Yours faithfully,
Kokaku Kidotai
What could be the reason for the "auditd" process to use almost 400% (roughly 397%) for over 425 hours (431 hours before being suspended)? The process "auditd" was called by the system user "Apache". The box is running CentOS 6 with zPanel, two sites and a private PPTP VPN.
top:
Any idea where to start the investigation from? I totally have no idea but I want to solve this issue.
Yours faithfully,
Kokaku Kidotai
Last edited by a moderator:
