No chance I am clicking that link lol.
here is what the link says then. B)
Back in May of this year, Symantec released an avisory entitled
SYM06-010: Symantec Client Security and Symantec AntiVirus Elevation of Privilege. Those that took the time to read it beyond the title noticed that this isn’t just a local privilege elevation exploit. It’s an out and out remote stack overflow using a specific service (TCP port 2967). We started tracking possible exploit activity for this vulnerability in early June using an ATF policy to detect scans and exploits, with our thinking that someone would surely take an interest. Activity for this policy quickly dropped off our radar, buried underneath some juicy Windows and VNC holes that people focused on. We didn’t see many scanners for this service, and only a burst of a scan early last week.
That is, until now, in late November, when we see a bot using an exploit for this (and lots of people
are curious). We had a look at the bot, and found that it’s a new exploit plugin for a garden variety SDBot. This thing’s a beast! It’s huge, not unlike a bloated bot that someone’s thrown everything into. A partial list of the capabilities this puppy appears to have:
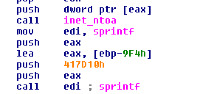
- SYMC06-010 exploit (TCP port 2967)
- NetAPI (MS06-040), TCP port 445
- DDoS and packet flooding (SYN, ACK, ICMP, UDP floods, for example)
- Password theft and packet sniffing
- It can enumerate other installed malware
- The usual bunch of access capabilities
- The usual bunch of brute force attacks, downloads, upload, proxy checks, etc …
And it tends to do it in the usual bot way, meaning inefficient and slow. Not surprising. This bot requires some reasonable reversing skills and tools; it will look for debuggers and tracing tools, and tries to spot a VMWare installation. If you fail to get past that, it bails, but not until it makes sure it will start on the next reboot. It doesn’t unpack fully in memory, either, and uses the Themida packer. Most sandboxes out there (Norman, CWSandbox) are blind to it. The malware starts, loads a few DLLs, notices it’s being traced, and goes away. Sandbox reports are very, very useless in this situation.
If you’re concerned you’re going to be targeted and that your network is at risk from this bot, you’ll have to block a lot of the standard bot stuff, including ports 139, 445, 2967 (for that Symantec exploit), 1434, and so on. If you haven’t updated your Windows boxes, do so; if you haven’t updated your Symantec clients, do so. Follow the link above for the patch information. Specifically for that bot, it goes to the IRC server at
www.flackware.info on TCP port 6667. This currently resolves to 4 IP addresses. Blocking that at the DNS level or using a firewall policy should prevent the bot from getting additional commands.

