wlanboy
Content Contributer
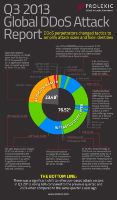
We all know about DNS amplification attacks (open relays) but now time servers are used to DDOS hosts too.
The Network Time Protocol is used to synchronize computers across the world against centralized servers to within a fraction of a second of coordinated universal time (UTC).
It uses the port 123 on UDP.
NTP is susceptible to main-in-the-middle attacks - just spoof the source.
NTP amplification attacks work quite simple. Ask for the latest clients and get back about 600 ip addresses of the latest connections:
ntpdc -n -c monlist <ip of ntp server>
The request packet is 234 bytes long. A busy server with the maximum of 600 addresses would send 100 packets (6 addresses per packet) for a total of over 48kb - that's a 200x amplifier.
NTP from version 4.2.7 on does not have the command "monlist".
If you don't have access to this version you can disable monlist:
nano /etc/ntp.conf
and add following line:
disable monitor
Another solution would be the NTP Autokey Authentication.
And there is allready a project scanning for open NTP servers: OpenNTPproject.org.
The Network Time Protocol is used to synchronize computers across the world against centralized servers to within a fraction of a second of coordinated universal time (UTC).
It uses the port 123 on UDP.
NTP is susceptible to main-in-the-middle attacks - just spoof the source.
NTP amplification attacks work quite simple. Ask for the latest clients and get back about 600 ip addresses of the latest connections:
ntpdc -n -c monlist <ip of ntp server>
The request packet is 234 bytes long. A busy server with the maximum of 600 addresses would send 100 packets (6 addresses per packet) for a total of over 48kb - that's a 200x amplifier.
NTP from version 4.2.7 on does not have the command "monlist".
If you don't have access to this version you can disable monlist:
nano /etc/ntp.conf
and add following line:
disable monitor
Another solution would be the NTP Autokey Authentication.
And there is allready a project scanning for open NTP servers: OpenNTPproject.org.