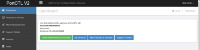
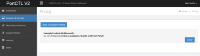
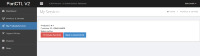
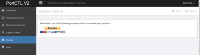
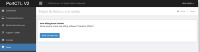
That's a way to trick security scanners, which usually try to interpret SQL errors to their advantage.Looks interesting. I'm curious why you would need to display an error to "log hacking attempts". This is obviously just an error showing one of your queries is using an invalid syntax, most likely with LIMIT in the wrong place. As a developer myself, there should be no reason for you to purposefully display a MySQL error to an end user. Any sort of logging should be done behind the scenes.
It's there for laughs, not very professional tho