Mohammed H
New Member
Hi There,
this module was developed in 2013. I wanted to share it with you so we can all benefit from it. and may be extend it.
Description :
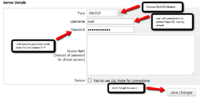
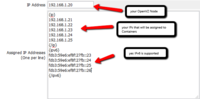
This is a server provisioning module made for WHMCS. it can help server administrators or VPS server providers to Create, Terminate, Suspend, Unsuspend containers on remote nodes using php ssh2 extension.
Features :
https://github.com/mohammedhs/XSLOVZ
I hope that community will report bugs/security issue and feedback to extend it's functionality.
this module was developed in 2013. I wanted to share it with you so we can all benefit from it. and may be extend it.
Description :
This is a server provisioning module made for WHMCS. it can help server administrators or VPS server providers to Create, Terminate, Suspend, Unsuspend containers on remote nodes using php ssh2 extension.
Features :
- Create, Terminate, Suspend, Unsuspend Containers remotely.
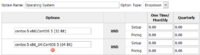
- Count bandwidth through external perl script (included in repo) and save bandwidth stats in database to count overusage bandwidth.
- Display basic stats like current HDD, Memory, Bandwidth for your clients.
- Clients have the ability to Reboot, Shutdown, Boot, their containers.
- Admins have the ability to Suspend, Unsuspend, Add extra IPs.
- XSLOVZ Overview
- Configure the module with your WHMCS and install ssh2_extension on your WHMCS server
- Notes on OpenVZ installation
- Configure Bandwidth Counter
https://github.com/mohammedhs/XSLOVZ
I hope that community will report bugs/security issue and feedback to extend it's functionality.
Last edited by a moderator: