You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Wow, that's bad luck. Hopefully all their backups restore properly.
On a side note, why did they have IPMI on a public facing network? I understand it may have been their decision but when you have 8 nodes wouldn't the provider be a bit flexible with the request?
On a side note, why did they have IPMI on a public facing network? I understand it may have been their decision but when you have 8 nodes wouldn't the provider be a bit flexible with the request?
I wouldn't say it was bad luck, they had a forward facing out of band management interface. I don't understand why any would do that, but even so this is after several security researchers noted of numerous security issues. There is no reason to have an interface that doesn't really receive updates connected to the internet. Especially one that can completely nuke a server.Wow, that's bad luck. Hopefully all their backups restore properly.
I covered that in my second paragraph.I wouldn't say it was bad luck, they had a forward facing out of band management interface. I don't understand why any would do that, but even so this is after several security researchers noted of numerous security issues. There is no reason to have an interface that doesn't really receive updates connected to the internet. Especially one that can completely nuke a server.
drmike
100% Tier-1 Gogent
Thanks for posting this @MartinD, someone sent it to me and I was busy 
Text of it for others to find/read...
Text of it for others to find/read...
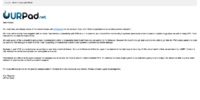
Dear,
You most likely are already aware of the current issues with URPad.net and its services. If you aren't then congratulations on avoiding service disruption.
We have, unfortunately, been targeted with an attack. Specifically a vulnerability with IPMI on our LA systems, as a result of this vulnerability 8 systems were wiped which caused our website to go down as well as many VPS'. Rest assured that no data has been stolen.
We were aware of the vulnerability and we took recommended action to temporarily block it until there was an update for the firmware. However this wasn't enough and a person was able to get into the IPMI access panel and reset our systems. We managed to catch it while it was happening and completely locked all our systems to prevent any further damage.
Backups of your VPS' are being loaded as we type so your data is not lost forever. But due to the extent of the damages it has resulted in multiple days of restoring. At this current point in time, we are restoring "LAB4". Once it is fully restored we will be moving onto the next system and so on.
Time frames are difficult at this point because the damages are so severe, we have to restore multiple hundred VPS'. An estimate for every single system to be restored is going to be 2-3 days. We should be able to give a closer estimate on your service uptime if you contact support.
For those affected by this we will provide compensation in the form of 2 extra weeks on your service. Please contact support to arrange this.
Kind Regards,
Last edited by a moderator:
BrianHarrison
Member
Anyone know what brand/vendor/version of IPMI they were running?
That sucks considering that the bug has been around for a while just now making news. Why would anyone use a ipmi device on a public interface makes no sense.